At the enterprise level, every security vulnerability needs critical attention, especially if you’re dealing with sensitive user information or company data. And since most large businesses have their own web applications with potential vulnerabilities, every organization needs to prioritize identifying and patching these security risks.
To secure your digital assets, your team first needs to understand the most common threats and vulnerabilities. Then, they can use this knowledge to patch holes and prevent attackers from exploiting them.
Below, you’ll find the 16 most common web application vulnerabilities, followed by a few key strategies for mitigating them, including using a vulnerability scanner like WPScan.
What is a web application vulnerability?
A “vulnerability” in a web application (or any type of software) is a flaw in its design, implementation, or configuration that gives attackers an opening. As the name suggests, vulnerabilities leave your site exposed to potential attacks, which can come in a variety of ways.
Web application vulnerabilities can compromise your organization’s security and data integrity. Depending on the goal of the attack, malicious actors may gain unauthorized access to sensitive information, leading to a full-on breach.
Typically, organizations uncover vulnerabilities through security audits or standard review processes. Once your team identifies a vulnerability, it’s your organization’s responsibility to patch it as soon as possible.

“Patching” is the term used in web application security to indicate fixing a vulnerability. Patching methods will depend on the type of security issue you’re dealing with. Usually, this process involves updating the web application, which should happen in a testing environment to ensure the fix works.
The importance of knowing common vulnerabilities
So, why do you need to know the most common web application vulnerabilities?
As we mentioned, there can be serious consequences for your enterprise if you don’t discover and patch them in time. You could end up facing everything from a minor hack to a widespread security breach.
Since you’ll need to notify your clients or customers in the case of a serious hacking event, this can also lead to lasting damage to your organization’s reputation. You may also face lawsuits and incur costs associated with mitigation and recovery (like offering free credit monitoring for millions of people).
The good news is that vulnerabilities don’t exist in a vacuum. If you use any popular software, you can find information about past and present vulnerabilities, security patches, and their general security status.
The more popular an application is, the bigger the community that will share information about its security issues. That can include regular users, developers, security experts, researchers, and even the official web application creators.
To put it simply, staying on top of security research that concerns your software can give you a leg up on patching vulnerabilities before attackers can exploit the opening.
16 common, yet critical, web app vulnerabilities
Now, let’s explore the most common types of web application vulnerabilities. Keep in mind that a lot of this information ties back to WordPress, but also applies to any kind of enterprise‑level software.
1. Components with known vulnerabilities
By components, we mean software that integrates with your organization’s web application. This can be third‑party software that connects via an API, or plugins and extensions that directly interact with the application’s code.
As a rule of thumb, every component that you add to an application can be a source of vulnerabilities. Depending on the software, you might not have access to its codebase or be able to verify that the developers followed proper security practices.
It’s essential that your team analyzes every component you add to a web application and ensures that it doesn’t open the door to attacks. In that scenario, it’s your organization that can pay the price, even if the software doesn’t originate from your team.
2. Outdated and unpatched software
Outdated software poses the biggest risk in terms of security to web applications, bar none. For example, if you keep WordPress core software up to date, your organization’s web applications will face fewer vulnerabilities and become less open to attacks.
Older versions of the software may come with known vulnerabilities. In the vast majority of cases, there’s little reason not to update software as soon as new security patches or major releases become available.
When it comes to enterprise web applications, it’s always a smart move to test changes and updates in a staging environment. This will enable your team to iron out technical issues and ensure that updates don’t cause new problems while they’re working on fixing security vulnerabilities.
You’ll also want to ensure that you always have a backup on hand.
3. Security misconfiguration
Even the most secure software is only as good as its configuration. Take a firewall — without the proper configuration, the software can block the wrong connections. This can lead to blocking benign traffic while overlooking known malicious IPs or types of attacks.
Every enterprise‑level organization can benefit from regular security audits that go over software configuration settings. This applies to any software involved in the development of the web applications you use, and the applications themselves.
Even secure configurations can become outdated. Periodic reviews will ensure that your team doesn’t overlook needed updates to settings that can prevent new types of attacks.
It’s also essential that your organization maintains comprehensive security logs. These logs should keep track of who makes changes to security settings. This will enable you to trace the source of security vulnerabilities in case they have to do with human error.
4. Broken authentication and session management
This type of vulnerability can appear if an application’s authentication procedures aren’t airtight. Basically, you’ll want to offer a secure login and access experience that only works for authorized members of the organization.
Secure authentication procedures can minimize the risk of attackers gaining access to your web applications. There are several ways to do this, from enforcing secure password policies to using multifactor authentication (MFA). Some user configuration settings, like session timeouts, can also drastically increase the site’s security.
At the enterprise level, authentication procedures should be considered critical. Your organization might be dealing with sensitive information and any unauthorized incursions can lead to devastating consequences, not limited to loss of customers and monetary fines.
It’s important to note that even if attackers gain access to an application by circumventing or breaching authentication protocols, they shouldn’t be able to cause any lasting damage unless they’re using an administrator account.
With this in mind, every account for a team member in your organization should only have the exact level of permissions they need to perform their tasks. Any further permissions can put your application and organization at risk.
5. Cryptographic failures and sensitive data exposure
Any sensitive data you store in a web application should be encrypted. That applies to everything from user details to login credentials.
Using strong encryption means that even if attackers get access to an application’s database, they won’t be able to do anything with the information they find inside. Without the keys to break the encryption, all they’ll have is a collection of characters that can’t be parsed into valuable information.
It’s your team’s responsibility to ensure that any applications they use or develop employ encryption properly. That means using cryptographic methods that can withstand sophisticated attacks.
In the case of web applications, this also means securing data during transmission. That’s why every website with decent security standards uses the HTTPS protocol, which significantly reduces the risk of data being intercepted during transmission.
6. Insecure direct object references (IDOR)
Insecure direct object references, is a kind of vulnerability where unauthorized individuals can gain access to private files or change data by simply modifying a basic user input. This could be a parameter (like on a URL) that opens a file directly without checking user permissions. An example of this is having a website that enables users to browse directories.
If an attacker can browse directories openly, they’ll have a roadmap to your site’s functionality. They can try to execute and modify files and, even if they’re not successful, simply having access to enough information to pull this off is a significant vulnerability.
In a secure environment, the application will deny access to any internal elements to outside parties. This means that end users shouldn’t be able to see directories, database keys, or any other information they can use to gain insight into how an application works (and how to break its security).
7. API and web service vulnerabilities
An API enables integration and communication between different software. APIs are used extensively in modern web applications because they enable different software solutions to work together nearly seamlessly.
The downside of using an API is that it introduces an application to potential vulnerabilities. APIs continuously retrieve and send data between software, so it’s an ideal channel for attackers.
A secure API should require proper authentication and authorization to be used. Likewise, it should only transmit data over secure channels and limit the rate at which users have access to data.
Rate limiting means that even if attackers can access the API, they won’t be able to launch distributed denial‑of‑service (DDoS) or brute force attacks using it. This makes the API more secure and keeps it functioning properly for sanctioned applications.
8. SQL injection (SQLi)
A SQL injection is a type of attack that targets the database through vulnerabilities in an application. These vulnerabilities enable attackers to execute malicious SQL queries, which they can use to access sensitive information.
Attackers might also use SQL queries to manipulate critical data and gain access to the entire information system. Typically, these types of attacks are possible when applications don’t validate and sanitize user inputs.
That means attackers can use simple web forms to submit malicious SQL code and have the server execute it. SQL injection attacks are potentially damaging at every level, from small to enterprise‑level projects.
9. Cross‑site scripting (XSS)
Cross‑site scripting (XSS) is a type of vulnerability that enables attackers to inject scripts into pages so that other users execute them. Attackers can use XSS to gain control over user sessions, steal credentials, and manipulate users in a multitude of ways.
This type of attack is possible in scenarios where developers don’t restrict the potential sources of executable scripts or use unsecured frameworks that don’t prevent XSS attacks by default.
Input sanitization also plays a significant role in preventing this type of attack. This is because proper sanitization can prevent attackers from submitting malicious code and scripts that your application will execute.
10. Cross‑site request forgery (CSRF)
Cross‑site request forgery (CSRF) works by exploiting browsers to submit unauthorized actions to an application after a user is authenticated. CSRF attacks exploit session cookies, which provide users with access to the application even if they’re not currently using it since they’re already logged in.
If the application isn’t properly secured, it will take the requests at face value since they come with the appropriate session credentials. An example of this would be an attack on a banking website exploiting a user’s session.
Assuming the bank application doesn’t validate the session information or force the user to login again, an attacker will be able to access their account. From then on, they might be able to wreak financial havoc.
That’s an extreme example, but CSRF attacks can be substantially damaging to enterprise‑level web applications. This type of application typically contains sensitive user data and if it’s leaked, your organization can pay dearly for it.
11. File inclusion vulnerabilities
File inclusion vulnerabilities enable attackers to include files in a web page using a script. Attackers can use this type of vulnerability to launch multiple types of incursions, including XSS and data theft.
This type of vulnerability falls into two categories. The first enables attackers to execute files on the server and the second enables them to execute remote files.
Running local server files can give attackers access to sensitive information. On the other hand, running remote files offers the perfect opportunity for executing malicious scripts that directly affect users.
12. XML external entities (XXE) attacks
XML external entities (XXE) attacks rely on poor XML parsing from an application. Attackers submit XML inputs including references to external files or scripts and the application enables these inputs to run.
There are relatively simple ways to mitigate this vulnerability. The most common methods include validating and sanitizing inputs, as well as disabling the use of external files by the application’s XML parser.
13. Server‑side request forgery (SSRF)
A server‑side request forgery (SSRF) attack takes advantage of a security vulnerability to enable attackers to instruct a web application to make a request to another domain. This can be useful to bypass web application firewalls (WAFs) that block access to known malicious traffic but will enable an application in good standing to bypass their security.
The types of requests attackers make will depend on their goals.
An SSRF attack can request access to internal URLs to reveal sensitive information or be used to map your organization’s network. This is critical information that malicious actors can use to determine how to bypass other security measures.
14. Insecure deserialization
Deserialization involves converting data from a secure or “serialized” format back into an object. Serialized formats include options like binary, XML, and JSON, among others.
Applications favor these formats for storing and transmitting data since they’re secure and easy to parse. Insecure deserialization involves manipulating these files to inject malicious data or code into them.
This attack can alter the way in which the application works due to the malicious input. An example of this would be modifying the contents of a cookie that can perform malicious actions, like executing code, once it’s deserialized.
15. Unvalidated redirects and forwards
Unvalidated redirects and forwards involve sending users to other applications or websites with malicious purposes. Typically, redirects and forwards are used to keep users from seeing unwanted or outdated content and to point them to other sites.
You can configure redirects at the application or server level, as well as through load balancers, domain name systems (DNS), and content delivery networks (CDN). Configuring redirects at the application level requires access with high enough permissions, which is possible if the application is vulnerable.
The danger of unvalidated redirects is that they might affect a large number of users before you detect them. This can be a way to implement mass phishing attacks. So, at best it can negatively impact user trust, and at worst it can cause your customers to be hacked or scammed.
16. Insufficient logging and monitoring
Enterprise applications should implement comprehensive logging practices. This means tracking the actions that take place on every level, along with who performed each one.
Security logs provide auditable trails. You can use them to identify the origins of web application vulnerabilities, malicious actors within your organization, and regular cases of human error.
Not logging this type of information constitutes a basic security vulnerability. Even if your application is properly secured, a lack of logs will lead to longer troubleshooting and patching processes since you’ll have a harder time tracking security incidents.
Five proven steps to mitigate web app vulnerabilities
Now that you have a firm grasp of the types of web application security vulnerabilities your organization can face, it’s time to talk about proactive security measures. Here are five proven steps to mitigate web app vulnerabilities.
1. Use a proven, comprehensive vulnerability scanner
A vulnerability scanner is a tool you can use to identify the potential attack vectors for a piece of software. In the context of a web application, we’re talking about a tool that can help you identify vulnerabilities and (potentially) provide you with information on how to patch them.
Vulnerability scanners like the WPScan plugin, which is only available for enterprise organizations, do this by analyzing your site’s components and code, and comparing it against a database of known vulnerabilities.
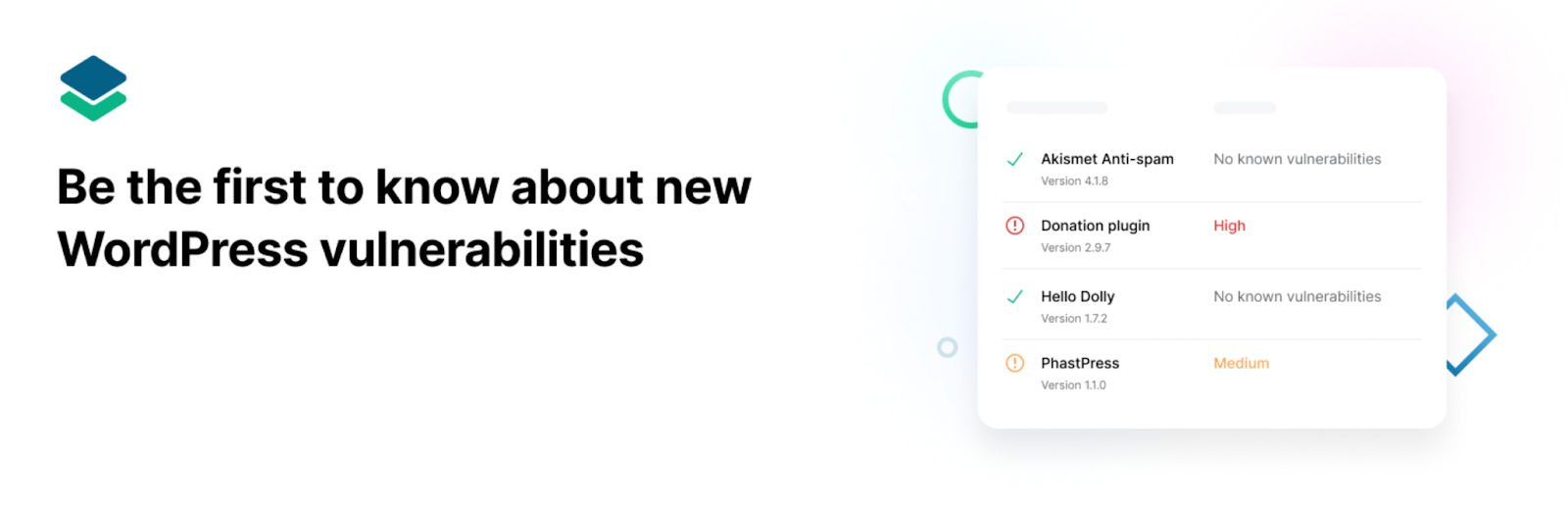
Ultimately, any vulnerability scanner is only as good as the database it has access to. If your organization uses WordPress, WPScan is the best choice because it maintains the largest database of WordPress vulnerabilities and security issues.
It’s important to note that your organization will also need to use a tool that has full access to the web application it’s analyzing. Without that access, the scanner won’t be able to uncover critical vulnerabilities.
Your organization may also opt to use the WPScan CLI, which provides vulnerability scanning from an outside perspective. It shows weaknesses that attackers may be able to exploit without having direct knowledge of the exact software and versions you’re using. In this way, it acts as a penetration testing tool and works together with the WPScan plugin to provide a comprehensive look at your web application’s security.
2. Deploy a web application firewall (WAF)
A WAF is software designed to protect web applications by monitoring incoming and outgoing connections. The WAF uses a set of rules to determine which connections to filter and which to let through.
In practice, a lot of types of malicious attacks follow similar patterns. If your web application is dealing with a DDoS attack, a properly configured WAF will stop it by limiting the number of incoming connections to the server.
A WAF provides the perfect example of how security configurations can leave a web application vulnerable. Depending on your security team’s expertise and the configuration settings they choose, your application might never have to face a direct attack as the firewall will filter incoming malicious traffic.
In practice though, this is seldom the case, since attackers can be incredibly sophisticated. Depending on your organization’s standing, your applications might be the targets of constant attacks and a WAF is simply one line of defense in what should be a comprehensive toolset.
3. Maintain software patches and updates
Maintaining software patches and updates is perhaps the most important security measure you can take when developing a web application. The application itself needs to receive regular security audits and updates to patch any vulnerabilities you discover.
In case you’re using third‑party tools like plugins, they also need to receive regular updates. Most popular plugins receive periodic updates to add new features and to fix security issues as they’re discovered.
Failing to update software puts your application at risk of attacks and data breaches. This is a situation your organization never wants to find itself in, especially since updating software is typically a simple process. Moreover, reputable software will let you know when updates are available, which means there’s no excuse not to install them.
4. Adopt and adhere to secure coding practices
Any application is only as secure as its underlying codebase. If your organization’s developers don’t adhere to secure coding practices, it leaves the software open to attacks.
The concept of secure coding practices involves avoiding vulnerabilities due to human error. One common mistake that comes up with web applications is a lack of input validation and sanitization.
“Input validation” means reviewing data that users submit through forms within the application. Without proper validation, the application will let users submit any kind of input, including malicious code.
Code “sanitization” involves taking user inputs and removing anything that can be perceived as malicious. These are two examples of secure coding practices. Overlooking them can lead to an application that’s ripe for attack.
Proper coding practices require team leads who oversee and guide other developers to write code that’s clean, well-documented, and secure. Naturally, this is more time-intensive than outputting code quickly and waiting for things to break, but the implications of this kind of shortcut are simply too severe — especially for large companies.
5. Implement MFA and role‑based access control
MFA requires users to enter additional credentials beyond a username and password to access a system. What these credentials are will vary depending on the implementation.
Two‑factor authentication (2FA) is the most common type of MFA. This system typically sends users a one‑time code via email, SMS, or an authenticator app. Without this code, they won’t be able to access the application.
This increases security exponentially because it means even if attackers gain access to credentials, they won’t be able to use them without the additional verification factors.
When you combine this with role‑based access control, you have the foundations of a secure system that will keep your enterprise applications safe. Role‑based access means that each user has a “role” or type of account which only has a set level of permissions.
Permissions determine what users can do in a system. In any web application, the administrator should be the only account with full permissions. Every other user access role should only have the minimum level of permissions to perform their duties.
In practice, this won’t affect how your team performs their job. What this accomplishes is reducing the risk of attackers inflicting damage on your application even if they break into it, since they’ll be limited by roles.
Frequently asked questions
What’s the first step to securing a web application against vulnerabilities?
Understanding the most common vulnerabilities that can affect an application is the first step to securing it. If you know what vulnerabilities to look out for, you’ll be able to identify and potentially patch them.
The most efficient way to do this is by using a vulnerability scanner. Depending on its efficacy, you’ll be able to identify vulnerabilities nearly immediately and patch them before they become major security issues.
How often should I scan my web application for vulnerabilities?
You should scan your web application for vulnerabilities as often as possible. If you have access to automated vulnerability scanning tools, like WPScan, you’ll be able to work much more efficiently.
These tools regularly scan your application’s files, monitoring for security issues. This consumes a small number of resources in terms of hardware, but it’s a tradeoff that an enterprise‑level application can easily make in exchange for increased security.
What is WPScan and what does it do?
WPScan is a comprehensive and open‑source database of WordPress vulnerabilities. A broad range of people contribute to growing and improving the database, including developers, security researchers, and users.
You can leverage that database in several ways to improve your enterprise application’s security. The WPScan CLI Scanner offers a simple way to test your application’s defenses for “weak” spots, as a penetration testing tool.
If you want a full vulnerability analysis, enterprise organizations can also use the WPScan plugin to browse your website’s software for known vulnerabilities. The plugin gets full access to the site, which makes it an incredibly effective scanner.
How does WPScan keep its vulnerability database updated?
WPScan is an open‑source vulnerability database. That means anyone can contribute to it by submitting reports on newly discovered security issues.
The WordPress community is incredibly active and there are a large number of contributors that submit reports to the WPScan database. Among them, you have regular users, developers, and security experts alike.
WPScan: The leading vulnerability scanner for WordPress sites
When you’re in charge of web security for an enterprise‑level business, being aware of the most common web application vulnerabilities is crucial. This way, you can then take the appropriate actions to protect users and your company’s sensitive data.
If your organization uses WordPress, leverage WPScan’s vulnerability database to keep your web applications safe. WPScan offers the largest database of WordPress vulnerabilities and several ways to take advantage of it.
Talk to our team today to see if your organization is a good fit for WPScan.